Originally published by The Fifth Column News on Mar 18th, 2015 under a Creative Commons Attribution-Share Alike 3.0 License.

Ft. Meade, MD (TFC) – Back in June 2014 I wrote an article; Don’t Ask for your Privacy, Take it back for the Reset the Net campaign.
The only reason why mass surveillance works is because most of our communications are being sent in plain text, as easily read as you are reading this very article. Whether this is done willingly by the service provider or maliciously by the Government using devices and exploits without their knowledge, Encryption will keep (some of) your rights in tact, for now.
While I do admit there is a modest barrier to entry into the realm of secure communications, there is a number of ‘Out of the Box’ solutions emerging to attempt to reduce this barrier. I will detail these still in development solutions in the footer, and cover some of the more established solutions that require a small amount of setup next. (With a pictorial guide)
Secure instant messaging: Pidgin (w OTR plugin, Mobile users Get ChatSecure for Android or ChatSecure for iOS.)
Hide your IP (with exceptions!): Tor (Mobile users Get Orbot for Android.)
Encrypted GSM/SMS: TextSecure & RedPhone (Android only, iOS users get Signal 2.0)
On the complaints about Tor, Let me detail a few of the weakness that exist in Tor so that you may be able to understand its strengths. Tor was (initially) developed and funded by the US Government to give itself plausible deniablity for its own illegal and malicious actions against businesses and countries worldwide. If only the US Government used Tor it wouldn’t be very Anonymous, So it has to be a free for all to provide anonymity. That said, The Government doesn’t like supporting malicious actors other than itself. So, Darknet sites (The .onion network) were attacked. The reason this attack worked is for two reasons. One, Using Tor in a browser provides a wide attack vector via the Flash and JavaScript scripting engines. A script in Flash or JavaScript can report back the IP Address in the context of that code, before it passes over Tor. This is because the code is running locally in your browser and not on the server which does not know your IP address. Two, If every Tor node you are using is in fact owned by the US Government, a top-down view of all US Government nodes can in theory reveal your IP as an educated guess, but it is not conclusive.
Using Tor outside of a browser and not on the Darknet/.onion network will defeat this attack. Me personally, when I use Tor. I exclude all nodes that reside in a FVEY (Five Eyes) Member country. That is US, CA, AU, UK and NZ. I use an open source project called AdvTor to do this.
Pidgin is a messaging client that supports numerous protocols. The one I will focus on is XMPP, previously known as Jabber. The XMPP server I use is creep.im, You can add me using [email protected]. Here is a list of many XMPP servers.
There is no reason Pidgin shouldn’t be the MSN or ICQ of this decade. Most people have resigned to using Facebook for their messaging needs, But this is a horribly insecure centralized target for … pretty much everyone. XMPP allows you to use any number of servers in any number of countries to route your conversations thru, all with full encryption.
Here is a quick pictorial on how to get started with Pidgin (w OTR plugin
Click Add…

Fill out the form as shown below, using your own username and password.


I am using Tor in this example. Simply Install Tor and run it, The defaults will work. If you don’t want to do this, select ‘No Proxy’. The main benefit here with Tor (or any proxy) is maintaining your location security from whomever you selected to handle your chat (creep.im in the example).

If all goes well you will get this screen. This is your actual registration so remember your password.

Confirmation that all is well.

Add your first buddy. Feel free to add myself, [email protected] or the demo account I just made [email protected]

When someone adds you, This is what it will look like.

The OTR plugin gives further security by providing even more encryption and buddy authentication via secret phrases and questions. But even just using Pidgin over say regular Facebook is a huge improvement.
With the OTR plugin installed, Go to Tools -> Plugins in Pidgin, Select ‘Off the Record Messaging and hit ‘Configure Plugin’ – Now press ‘Generate’

If all goes well.

Now you will notice a new menu when chatting with Buddies and some new notices

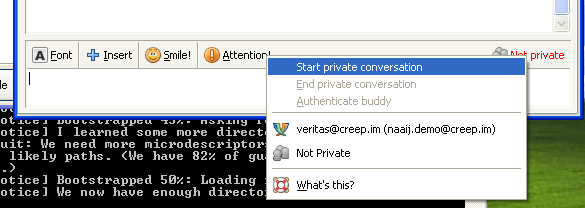
There are a variety of methods of ‘authenticating’ a buddy. The simplest is ‘Manual Fingerprint Verification’ – For your first time encountering people, this is good. It will ensure that your communicating with the same person on the same machine you originally added.

Alternatively there is a secret question and answer. This is good for people you know well. If you know them well enough you won’t even need to tell them the answer ![]()

And thats all there is to getting started with Pidgin.
Want to use XMPP on your phone? Get ChatSecure for Android. iOS users get Signal 2.0

A project that is currently in development I’ve been keeping an eye on is uTox. It allows for sharing of your desktop, a webcam, pictures, or just regular chat. All securely with encryption by design. Even better is that it is ‘zero configuration’ – You open it and you start chatting. No account or signup or registration.
From their Github
“With the rise of governmental monitoring programs, Tox, a FOSS initiative, aims to be an easy to use, all-in-one communication platform that ensures their users full privacy and secure message delivery.
..
The goal of this project is to create a configuration-free P2P Skype replacement. “Configuration-free” means that the user will simply have to open the program and will be capable of adding people and communicating with them without having to set up an account. There are many so-called Skype replacements, but all of them are either hard to configure for the normal user or suffer from being way too centralized.”
Windows uTox Updater (installs uTox if it isn’t already)
You will end up with a ridiculously long ‘Tox ID’ – For example, mine is 1E64DB1DFAEA2DBDE2204826CE649DA8A6BEC90C93BA16B7F557228B48FF234A1CD1876F268C. You can make this more human readable at www.ToxMe.se My human readable Tox ID is [email protected]

Another project worth watching is BitTorrent Inc’s Bleep which is basically the same thing as uTox. Currently Bleep ‘looks’ better, but Tox has many more functions at the moment. Add me on Bleep with this slightly less ridiculously long string: 32969203ae7c11f935ea0b3b561656eed0d891d57da9ecf7641e91a50769cc69
Governments will eventually break these encryptions or make them ‘illegal’ and brand everyone using them a thought criminal and/or terrorist. But until that happens, Any one of these tools are effective ways to thwart mass surveillance and take back at least a little bit of your privacy. For now.
Check out my other article on mass surveillance. As well as some great talks from NSA Whistleblower Edward Snowden
Nigel Todman is an Independent Journalist, Technical Consultant, Social Activist, Web Developer and Computer Programmer from Ontario, Canada. Add him to Facebook and/or Follow him on Twitter E-mail: veritas [at] vts-tech [dot] org [PGP]